Developing your website’s reputation and SEO ranking can take years of work and investment. The trouble is, the more traffic you gain, the likelier it is to attract unwanted attention from scammers and cybercriminals.
One common type of cyber attack website owners suffer from is domain hijacking. In this article, we’ll show you what it is, how to prevent it, and what to do if it happens.
Domain Hijacking Definition
Domain hijacking, often known as domain theft, is a type of cyberattack in which the offender changes the usage rights of a domain name without the consent of the original owner. It revolves around taking control of a domain name, removing access (and authorization) from the registrant, and giving it to another party.
Domain hijacking can be disastrous to a business and its brand and online reputation. Potential damages include:
- Loss of reputation,
- Brand associated with scams and malware,
- Inability to recover your domain name,
- Loss of access to your email domain,
- Hackers reading (and replying to) emails containing sensitive information,
- Legal liability,
- Data leaks,
- Financial damage (asset loss).
Once a hijacker takes control of the domain, they can use it for whichever purpose they choose, such as:
- Using the website for phishing,
- Sending and receiving emails from your customers,
- Affecting the performance of your website and/or app,
- Redirecting payments to a different bank account.
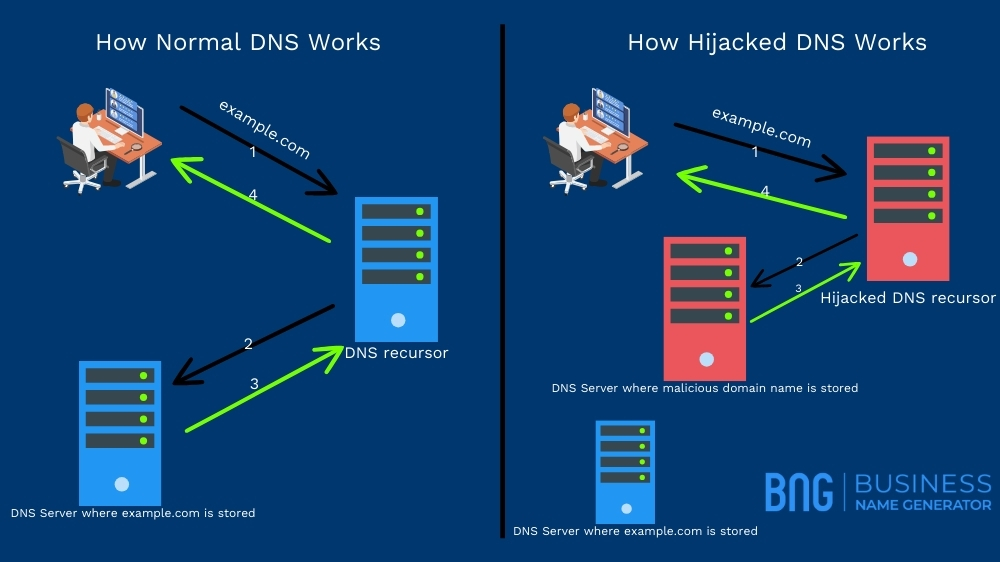
Domain Hijacking vs. DNS Poisoning
Both domain hijacking and DNS poisoning have the same goal of tricking users into visiting hacker-owned websites instead of a legitimate one. The way they go about it differs, as explained in the table below:
| Domain Hijacking | DNS Poisoning | |
|---|---|---|
| Who Gets Attacked: | Domain owner. | DNS server. |
| What Happens: | Hackers take over the domain by getting registrars to change owner records in the domain name system (DNS). | Hackers change DNS settings directly. |
| Where the User Goes: | They visit the same website now owned by hackers. | DNS servers point them to a different IP address (i.e., a different website). |
MORE: Domain spoofing
With DNS poisoning, cybercriminals can create an identical copy of your website via a cybersquatting domain on the new IP address and take control of any transactions. Alternatively, they can add malware, set up a phishing scam, or attempt to steal sensitive information from visitors.
How Does Domain Hijacking Work?
There are several ways domain hijacking takes place. The most common one is social engineering, i.e., tricking domain owners into sharing private information and login credentials. Another example revolves around following registration expiration dates and registering the domain name if the current owner forgets to do so.
A hijacker can gain access to your domain’s control panel or your email address. When the latter is the case, they can impersonate you and contact your registrar requesting to change ownership. Usually, they request to transfer the domain name to another registrar (located in another country), which makes recovery difficult.
If social engineering or taking over a registration fails, hackers can turn to technical methods. There are four types of technical hijacking:
- Router hijacking: It’s usually the first port of call for hijackers. A lot of routers use default passwords and have firmware deficiencies, leaving them vulnerable to unauthorized logins. Once they access a router, hijackers can modify settings or select a fraudulent DNS server as the preferred option.
- Local hijacking: It requires hackers to install Trojan malware onto your system and change your local DNS settings.
- Rogue hijacking: This type revolves around attacking your internet provider and changing records on its name server. It results in a large number of users of the same provider being redirected to a fraudulent DNS server.
- Man in the middle: Similar to DNS poisoning, man-in-the-middle attacks focus on intercepting communication between a user and DNS, providing users with a different IP address. This is possible only via non-encrypted DNS queries. The difference between this and DNS poisoning is that the latter affects DNS records, while the former targets users’ connections.
In rare situations, hijacking can also happen due to security vulnerabilities in your registrar’s system.
How Domain Hijacking Occurs
Domain hijacking can happen as easily as not signing out from your account, entering a password while on a public network, or forgetting to renew your subscription.
You might think that would never happen to you. Yet, according to the World Economic Forum, 95% of all cybersecurity issues occur due to human error. Amar Yasser El-Bably, PhD in Law and Police Sciences, states that the most often human errors leading to cybersecurity breaches include:
- Using weak passwords,
- Ignoring software updates,
- Trusting public WiFi hotspots and using them without a VPN,
- Performing unauthorized system changes,
- Using personal devices for work purposes,
- Not locking your device or signing out,
- Disabling security features,
- Sharing employee-issued devices with friends and family,
- Downloading unauthorized software,
- Misdelivery and misconfiguration.
Is Domain Hijacking Illegal?
Technically, domain hijacking is considered theft. However, since you haven’t lost any physical product, it’s hard to prove that a change of data in the DNS registry equates to having your diamond ring stolen. There are no international or U.S. laws that address this particular type of cybercrime.
What makes the whole thing difficult is that you need to file a court action in the country where the affected DNS server is located, not in your jurisdiction.
Domain Hijacking Examples
Having said that, there were instances where U.S. courts have found people guilty of domain theft. In 2017, an ex-employee who had login credentials redirected a business’s domain to an adult content website. A court in Arizona sentenced him to four years of federal probation and gave him a $9,000 fine.
There are also older instances, such as Stephen M. Cohen being arrested in 2005 after failing to pay $65 million for hijacking the domain name Sex.com.
One of the common damages of domain hijacking are data breaches, with the global average cost per data breach being $4.45 million. According to Statista, the following are the largest data breaches in the world as of 2023:
As you can see, the largest breach occurred in 2020, when the Cam4 data breach impacted 10.88 billion records.
How to Prevent Domain Hijacking
The best way to protect yourself from domain hijacking is to make sure it never happens. You should constantly seek out the latest developments in cybersecurity and check if your system is well protected. According to Cisco, cyber fatigue (failing to proactively defend from attacks) affects 42% of businesses.
You can prevent domain hijacking by doing the following:
- Set up two-factor authentication,
- Use strong passwords,
- Pick a reputable registrar,
- Secure your domain name,
- Enable auto-renewal of your registration,
- Use WHOIS privacy protection,
- Keep your systems updated,
- Check who has access to your domain’s control panel,
- Mark emails that request access to your backend,
- Make sure your contact information is up to date.
How to Recover Hijacked Domains
Unfortunately, there’s not a lot you can do once hijacking happens, which is why it’s paramount to do all you can to prevent it.
If you’ve been a victim of domain hijacking, you should reach out to your registrar immediately and inform them of the attack. The faster you notice the hijacking attempt and contact your registrar, the more chances there are they will be able to restore your ownership. Once a domain transfer is complete, your registrar can no longer help you.
At this stage, you can contact ICANN and get them to resolve the issue. This is a viable option if you have trademarked your domain name, which would allow you to invoke the Uniform Domain-Name Dispute-Resolution Policy (UDRP).
Finally, you can consider legal actions, but as we’ve said, there aren’t many laws (and they lack enforcement), and you’ll have to deal with jurisdiction issues as well.
If the hijacking occurs, try to establish a safe line of communication with your users and inform them immediately that your website is no longer secure.
MORE: How to change a domain name
Domain Name Hijacking vs. Domain Hacking
Although they sound similar, they are worlds apart. Domain hacking has nothing to do with cybersecurity. It’s a term that signifies a practice of combining top-level domains (TLDs) with the unique part of your domain name into a meaningful word or phrase.
For example, you can use a domain type that fits an expression (unroll.me) or an abbreviation in your industry (such as .io and .ai domains).
MORE: Domain name trends for 2024
Popular examples of domain hacking include:
- Instagr.am,
- Bit.ly,
- Cash.app,
- Pep.si,
- Nyti.ms.
Takeaway Points
The more your online business grows, the more interesting you will be to cybercriminals. You need to make sure that your domain name is safe and that your cybersecurity efforts are constantly evolving.
Losing a domain name to a hijacker can destroy your brand and make you lose your entire customer base. The trouble is, laws against hijacking are not yet established, so the best cure is prevention.
If you still haven’t chosen your domain name, we can help you. Use our domain name generator to get 1,000+ name ideas for free. We use AI to come up with catchy, memorable names for your website.
Frequently Asked Questions (FAQ)
- Sex.com,
- Google (Vietnamese ccTLD),
- Lenovo,
- 117 Microsoft subdomains,
- Cafax,
- Hypixel.
The most common way to commit hijacking is through social engineering, i.e., getting domain name owners to share sensitive information with you through various psychological tactics. Hijacking can happen when an attacker gains access to someone’s email and resets the passwords to their domain name registrar’s account.
Other ways involve a more technical approach, such as router hijacking, man-in-the-middle attacks, and DNS poisoning.